By Tony Anscombe, Chief Security Evangelist, ESET
We are currently experiencing an unprecedented global event. The outbreak of Coronavirus Disease 2019 (COVID-19) – now officially a pandemic – has caused apprehension globally, ultimately resulting in lockdowns, travel bans, panic buying, and financial market turmoil.
Scammers, too, have taken notice. Emergencies offer golden opportunities for con artists to launch fraudulent campaigns that feed off, and cash in on, the climate of concern. Against the backdrop of a disease that has so far caused more than 4,000 deaths and continues to spread, scammers have wasted no time in playing on people’s fears or evoking feelings of compassion.
Some cybercriminals clearly think that all their Christmases have come at once: an anxious population, vulnerable people at the highest risk, excessive demand for goods no longer in stock, and masses of disinformation sloshing around on social media – all this equates to a massive opportunity to prey on people and attempt to defraud them while they are at their most susceptible.
The scams can take various forms, and the ESET research team has shared a few examples of the despicable tactics seen in use recently.
Malicious news
As a major source of information on the outbreak, the World Health Organization (WHO) is among the most-impersonated authorities in the ongoing scam campaigns. In the example below, fraudsters pretend to offer important information about the virus in an attempt to get potential victims to click on malicious links. Typically, such links can install malware, steal personal information, or attempt to capture login and password credentials.
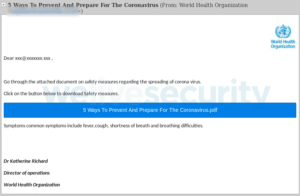
Figure 1. An email purporting to be from the World Health Organization
The WHO is aware that its brand is being used by scammers, so it provides advice on its website on how it communicates, and provides details of what it will or will not do in official emails. One of the most important points to note reads:
“Make sure the sender has an email address such as ‘person@who.int’. If there is anything other than ‘who.int’ after the ‘@’ symbol, this sender is not from WHO. WHO does not send email from addresses ending in ‘@who.com’, ‘@who.org’ or ‘@who-safety.org’ for example.”
The organization also advises to check the URL for any links in emails and that all web content will start with https://www.who.int/ and that no other domain is used. If there’s any doubt, then directly type the address into your browser.
Importantly, the WHO has not randomly started to email people who are not subscribed to a service. Consider navigating to the dedicated WHO site or to the sites of your respective national health care institutions, such as the Center for Disease Control and Prevention (CDC) in the United States or the National Health Service in the United Kingdom.
The real news can also be found on the trusted sources you normally visit to get your daily intake. Links in unsolicited emails do not have unique or breaking news stories.
In another example, the phishing website below is attempting to impersonate the Wall Street Journal (WSJ) and is supposedly reporting the latest COVID-19 news. We have redacted some of the URL for obvious reasons, but notice that it starts with ‘worldstreet’ and the wording on the webpage states ‘world street’.
Nevertheless, some visual consistency with WSJ branding is there in a clear attempt to subtly trick the visitor into thinking that this is the Wall Street Journal. The delivery of advertising on the site is generating revenue for the bad actors, even if no personal details are gleaned from the user.
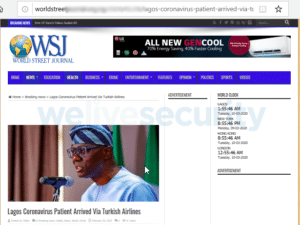
Figure 2. Hardly the real thing
Exploiting the charitable spirit
Another common type of scam doing the rounds is a tug on the heart strings that attempts to get the recipient to help fund the vaccine for children in China. There is, at the time of writing, no vaccine available and it is not expected to be ready for public use until next year.
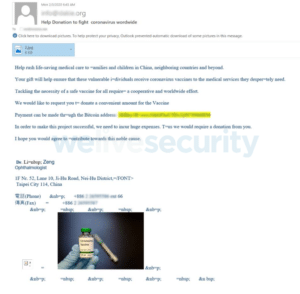
Figure 3. The fake charity
People who receive the coronavirus-themed emails are asked to send bitcoins to the attackers’ wallets. Despite this technique being only effective for a fraction of the users, when done on a global scale it can be financially attractive for the criminals.
Unmasked
In another type of fraud, scammers send spam emails in a bid to dupe the victims into thinking they can order face masks that will keep them safe from the novel coronavirus. What happens instead is that the victims will unwittingly reveal their sensitive personal and financial information to the fraudsters.

Figure 4. Fake offers for face masks
As you would expect, Google Trends shows that search volumes for terms such as ‘hand sanitizer’ and ‘face masks’ and are reaching unprecedented levels. With demand for these products outstripping supply, con artists have been increasingly targeting people who are looking to take protective measures. According to Sky News, fraudulent face mask sellers swindled people in the UK out of £800,000 (US$1 million) in February alone.
Face masks are in very limited supply, so be savvy about product claims and only purchase from a trusted vendor that you would normally trust with your order (and credit card details!).
Final thoughts
These are just a few of the examples of how cybercriminals are attempting to capitalize on the current climate surrounding the virus outbreak. This is an apt time for individuals and businesses to learn, or be reminded of, some of the most common ways criminals capitalize on people’s emotions (not only) during major events and emergencies.
Remaining vigilant, identifying and ignoring the product of cybercriminals and cyber-nuisances involved in scams or fake news is essential. Here are some of the basics that will help you stay safe:
- Avoid clicking on any links or downloading any attachments in unsolicited emails or texts from unknown sources, or even in trusted sources unless you’re absolutely sure that the message is authentic.
- Ignore communications that ask for your personal information. If necessary, verify the contents of the message with the apparent sender or the organization that they (seemingly) represent, and do so via a different medium than the received message.
- Be especially wary of emails that add to the sense of alarm and urge you to take immediate action or offer COVID-19 vaccines or cures.
- Look out for fraudulent charities or crowdfunding campaigns.
- Use reputable multi-layered security software that includes protection against phishing.

