The Health Insurance Portability and Accountability Act (HIPAA) establishes U.S. standards for protecting sensitive patient data.
For healthcare organizations and their business partners, achieving and maintaining HIPAA compliance requires implementing comprehensive security measures to avoid exposing protected health information (PHI). HIPAA regulations cover electronic files, paper records, and even business processes.
And as healthcare increasingly moves to digital operations, understanding and following these requirements has become more critical than ever.
Who Needs to Comply with HIPAA?
Covered Entities
HIPAA regulations mainly apply to healthcare providers, health plans, and healthcare clearinghouses that create, receive, maintain, or transmit PHI. Commonly covered entities include:
- Hospitals and medical clinics
- Physicians and dental practices
- Health insurance companies
- Medicare and Medicaid programs
- Medical billing services
Business Associates
HIPAA regulations also apply to any organization handling PHI on behalf of a covered entity. These business associates must sign formal agreements with the covered entities acknowledging their responsibility to protect PHI and implement appropriate safeguards. Typical business associates include:
- IT service providers and managed security providers
- Cloud storage and software vendors
- Medical device manufacturers
- Medical transcription services
- Law firms handling healthcare data
Key Components of HIPAA Compliance
Privacy Rule
The Privacy Rule forms the foundation of HIPAA compliance by establishing national standards for protecting individuals’ medical records and other personal health information.
It creates a framework of patient rights regarding their health information. Patients have the right to view, receive copies of, and request corrections to their health records.
The rule also establishes boundaries for the use and disclosure of health records. Healthcare providers must obtain patient authorization before sharing information. This applies to purposes beyond treatment, payment, and healthcare operations.
Security Rule
The Security Rule specifically protects electronic protected health information (ePHI).
This rule mandates that covered entities implement safeguards for electronic health information. These safeguards must be administrative, physical, and technical to protect confidentiality and integrity. Working with a managed IT provider can help organizations fulfill and maintain these complex requirements.
Safeguards on the technical front require the use of interconnected solutions. Together, these solutions form a comprehensive security framework. Such measures include:
- Access control systems that go beyond simple password protection to integrate unique user identification, automatic logoff procedures, and emergency access protocols.
- National Institute of Standards and Technology (NIST)-compliant encryption methods to protect health information stored on servers, workstations, and mobile devices.
- Audit control systems to track all system activity, creating detailed logs of who accesses PHI, when they access it, and what actions they take with it.
- Integrity controls to ensure that no individual or system alters or destroys PHI without authorization. Effective integrity control includes error-checking mechanisms for data transmission and storage, as well as secure backups of all electronic health information.
Enforcement Rule
The Enforcement Rule defines how the Department of Health and Human Services investigates potential HIPAA violations, conducts administrative hearings, and determines appropriate penalties. While HHS holds primary enforcement authority, it is not alone. Agencies, such as the Centers for Medicare and Medicaid Services, can enforce actions under their own procedures.
Steps to Achieve HIPAA Compliance
Conducting a Risk Assessment
A comprehensive risk assessment forms the cornerstone of any HIPAA compliance effort. The process begins with creating a complete inventory of all systems and processes that interact with PHI, including both electronic and physical assets.
A technical analysis includes network infrastructure, access controls, and security systems. Vulnerability scanning, penetration testing, and reviewing system configurations all help analysts form a complete picture of the organization’s digital footprint.
Organizations should also evaluate their physical security measures, including facility access controls, workstation security, and device management procedures.
Non-technical assessment areas include reviewing administrative procedures, workforce training programs, and incident response plans.
A complete risk assessment culminates in detailed documentation of all findings, including:
- Potential threats and vulnerabilities
- Current security measures
- The probability and potential consequences of various breach types
- Recommended remediation steps
- A timeline for implementing security improvements
Developing Policies and Procedures
A comprehensive HIPAA compliance program includes well-documented policies and procedures for protecting patient information. Policies might include (but aren’t limited to):
- Privacy and security standards
- Patient rights and access procedures
- Breach notification protocols
- Business associate management
- Documentation requirements
- Approved uses of workstations and mobile devices
Staff Training and Awareness
Organizations should strive toward creating a culture of compliance. Ongoing training for all workforce members who handle protected health information will help in this regard. Training should address both general HIPAA requirements and organization-specific policies, with content tailored to different organizational roles.
Data Encryption and Secure Access Controls
Modern healthcare operations need robust technical safeguards to protect ePHI. Managed cloud services can help organizations implement and maintain critical security controls for cloud-based data and tools, including end-to-end encryption, multi-factor authentication, and role-based access management.
Regular Audits and Monitoring
HIPAA compliance is an ongoing practice. Organizations must stay on top of evolving regulations, regularly conduct assessments to ensure continued compliance, review and update agreements with business associates, and monitor for potential violations and breaches in a process of continuous improvement.
Common HIPAA Compliance Challenges
Today’s healthcare organizations and their partners face an ever-growing list of security threats that challenge HIPAA compliance efforts.
Cybersecurity risks continue to grow more sophisticated, with ransomware attacks specifically targeting healthcare providers. Recent incidents have shown that attackers often exploit multiple vulnerabilities, combining social engineering with technical exploits to breach security systems.
Mobile devices present particular challenges for HIPAA compliance. That’s because the increasing use of smartphones and tablets in healthcare settings creates new potential access points for attackers. Mobile device management (MDM) solutions that enforce security policies, encrypt data, and remotely wipe lost or stolen devices can help defeat this threat.
In a related challenge, remote work options have expanded significantly, especially following the COVID-19 pandemic. Now, healthcare organizations must secure data against unauthorized access even as employees work away from the protection of on-site company networks. They need advanced authentication systems, secure VPN solutions, and comprehensive monitoring tools, among other safeguards.
Cloud computing introduces opportunities and challenges for HIPAA compliance. While cloud services can provide robust security features and simplified management, procedures and security tools differ from one cloud provider to another. So, organizations must carefully evaluate providers, and agreements should clearly define security responsibilities.
Working with a co-managed IT provider can help organizations navigate these technical challenges while maintaining security and compliance.
Consequences of Non-Compliance
Financial Penalties
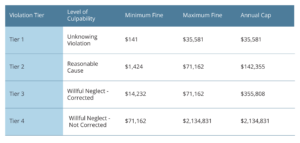
HIPAA violations can result in significant financial consequences. The Department of Health and Human Services Office for Civil Rights implements a tiered penalty structure based on the level of negligence, with fines ranging from $141 to over $2 million per violation.
Reputational Damage
The impact of HIPAA violations on an organization’s reputation can be severe and long-lasting.
Healthcare providers may experience the following:
- Decreased patient confidence leading to lost business
- Difficulty maintaining relationships with business partners
- Negative media coverage affecting market position
- Long-term impact on brand value
Legal Implications
Non-compliance with HIPAA can trigger legal consequences beyond regulatory penalties, including civil lawsuits, criminal charges, mandatory monitoring, and licensing investigations.
HIPAA Compliance in Practice
Real-World Examples
Recent HIPAA breaches highlight the diverse challenges organizations face in protecting patient information. All-too-common incidents include stolen devices that contain unencrypted patient data, unauthorized access by employees, and cyberattacks. These incidents demonstrate how seemingly minor security oversights can lead to significant breaches.
Success Factors
Organizations that successfully maintain HIPAA compliance typically share several key characteristics:
- Regular risk assessments and security updates
- Robust documentation and training programs
- Clear incident response procedures
- Strong vendor management practices
- Continuous monitoring and improvement efforts
Resources for HIPAA Compliance
For more information on HIPPA rules and compliance, visit the U.S. Department of Health and Human Services website, HIPAA for Professionals.
Building a Stronger Compliance Strategy
Ultimately, HIPAA compliance isn’t just about following regulations—it’s about protecting patient trust and maintaining the integrity of healthcare operations. As healthcare continues to digitize and cyber threats evolve, organizations must prioritize robust security measures and comprehensive compliance programs.
Whether you’re just starting your compliance journey or are well-practiced, keep in mind that HIPAA compliance is an ongoing process. It calls for constant vigilance and adaptation to new challenges.
Take the first step by assessing your current compliance status and identifying areas for improvement.
Need Help?
If you’re looking for Managed IT and IT Security support in meeting HIPAA requirements, Xantrion offers comprehensive managed IT and security services tailored to healthcare organizations.
We provide expert support for patient data protection and compliance in California, including these areas:
- San Francisco Bay
- San Jose and Silicon Valley
- Los Angeles
- San Diego
- Sacramento
If you’re looking for Compliance support in meeting HIPAA requirements, Xantrion offers comprehensive advisory services tailored to healthcare organizations.
HIPPA rules are about get an upgrade. Check out our recent article to learn more.
Frequently Asked Questions
Who Needs to be HIPAA-Compliant?
Any organization that creates, receives, maintains, or transmits protected health information must adhere to HIPAA compliance requirements. That includes healthcare providers, health plans, healthcare clearinghouses, and their business associates.
What Happens if I Don’t Comply with HIPAA?
Non-compliance consequences can include monetary penalties of up to $2,134,831 per violation, corrective action plans, increased oversight, and potential criminal charges. The reputational damage from HIPAA violations can also affect an organization’s ability to maintain patient trust.
How Often Should I Review My Compliance Policies?
Organizations should conduct formal reviews at least annually and update policies whenever significant changes occur in operations, technology, or regulations.
Can a Small Business Become HIPAA-Compliant?
HIPAA regulations are designed to be scalable, allowing organizations of any size to achieve compliance. Working with experienced IT partners can help even small organizations implement appropriate security measures efficiently.
What Is HIPAA in Cybersecurity?
HIPAA’s Security Rule establishes specific requirements for protecting electronic health information through technical safeguards, including access controls, encryption, audit controls, and secure transmission methods.
Xantrion can help you meet and exceed your HIPPA requirements. Contact us today, for a no-obligation compliance and cybersecurity assessment.

